4. February 2026 By David Metzler
With the C5 seal of approval for a secure and tested cloud
‘In recent years, the BSI's C5 requirements catalogue has become a spearhead that drives and supports cyber security in one of the most important areas of digitalisation: cloud computing. For digitalisation to be successful, it is extremely important that cloud services demonstrably have a generally accepted level of security.’
With these words, the Federal Office for Information Security (BSI) introduces the Cloud Computing Compliance Criteria Catalogue (C5), describing it as a confidence-building standard for cloud security.
Scalability, flexibility and efficiency have long been synonymous with the advantages of the cloud. These are some of the reasons why organisations use cloud solutions. However, outsourcing sensitive data and processes can also increase security risks. This is where C5 comes in: a structured and verifiable basis for cloud security for both cloud providers and cloud users. A structured catalogue is used to present requirements in a transparent and verifiable manner. The requirements include measures for access control, encryption, emergency management and data storage.
Am I affected? – How the BSI C5 helps with your secure cloud strategy!
The following illustration shows the circumstances under which the C5 could be relevant! In short: the C5 is necessary to avoid potential risks and compliance violations.
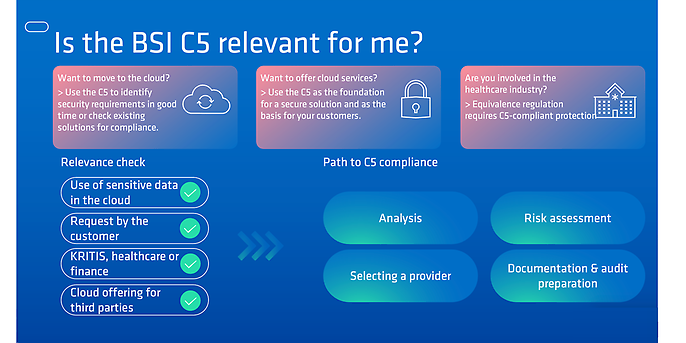
Organisations should address the issue of cloud security as early as the planning stage of a cloud project. The C5 can serve as a best practice standard here – regardless of whether you are a provider or a user.
If you work in the healthcare sector, the Digital Act applies in conjunction with the Equivalence Regulation, which requires a C5 certificate for cloud use in Section 393 of the German Social Code (SGB V). In particular, hospitals, medical practices and billing services must provide evidence of appropriate security measures and controls for health and social data since 1 July 2025, as well as proof of their effectiveness. Medical laboratories and accident insurance funds should also follow the C5 standard.
Organisations in the KRITIS or financial sector must also comply with the KRITIS Regulation and the requirements of DORA and BAIT. When using or utilising cloud services, the requirements and risk assessments of C5 should be taken into account. A C5 can also be used as evidence in accordance with Section 8a (3) BSIG.
When processing personal or confidential data in the cloud, adequate protection in accordance with the GDPR and C5 must also be ensured.
IT service providers who want to market their cloud services in these sectors should align their offerings with the C5 criteria from the outset. This ensures that the cloud service offered is set up securely, facilitates customer audits, and strengthens market acceptance and trust.
The BSI C5 as a tool of trust: content and structure
The cloud is more than just technology
We think end-to-end
adesso provides companies with comprehensive support on their cloud journey – from strategic consulting and customised migrations to secure operation and managed services. With an end-to-end approach, we combine technological excellence with industry knowledge to create real business benefits, increase agility and confidently meet compliance requirements.
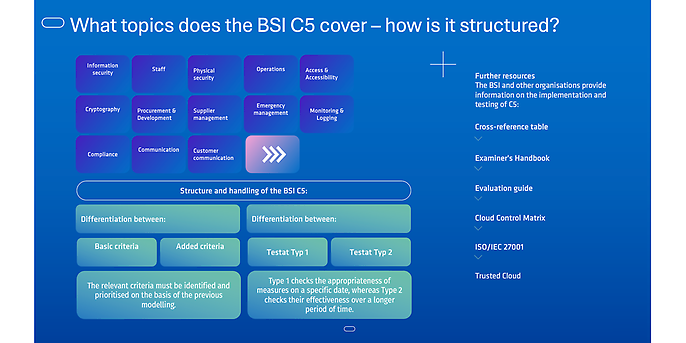
The C5 is a checklist for security in cloud environments. The list of criteria is divided into the above topics. Each topic area contains any requirements or ‘basic criteria’ and ‘additional criteria’, thus guiding you towards cloud security in a structured and comprehensible manner. Which topic areas and criteria are relevant for your organisation or need to be implemented by other stakeholders must be determined individually based on the protection requirements and modelling.
In addition to these criteria, there are supplementary documents or information, such as the BSI's evaluation guide and cross-reference tables, which can be used both for the structured review of existing attestations and for comparison with other standards.
A basic distinction is made between two types of attestations:
- Type 1 – checks the appropriateness of the measures on a specific date
- Type 2 – checks the effectiveness of implementation over a longer period of time
If your organisation uses cloud services for which a C5 attestation is available, it is necessary to systematically review it, assess responsibilities and identify any outstanding requirements.
If you want to extend the C5 to include data protection and contract design, you can use the ‘Trusted Cloud’ of the Federal Ministry for Economic Affairs and Climate Protection.
Next steps: From analysis to certification – how to get started
Implementation is not an IT solo effort, but requires the cooperation of various departments. Below we see the implementation process.
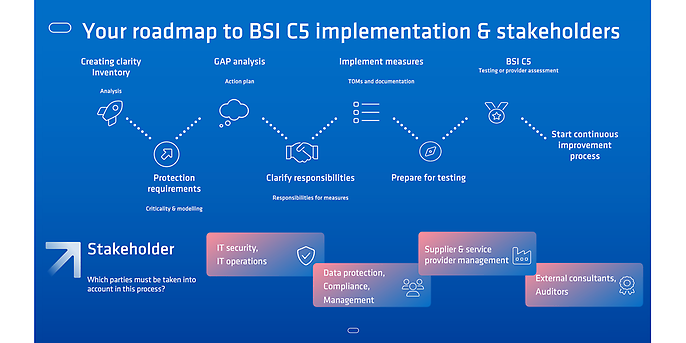
The first step on the path to C5 certification or a provider audit is to establish clarity. An analysis of the current situation helps to systematically record the services, data stocks, systems and existing evidence concerned. Only with a complete overview can risks and requirements be specifically derived.
Based on this, a protection requirement assessment is carried out. Here, the criticality of the data to be processed, the applicable legal framework and the clients to be considered are analysed. Based on this protection requirement assessment, the C5 requirements must be modelled. The aim here is to determine which requirements or ‘basic criteria’ and ‘additional criteria’ are relevant for your organisation.
A key step in the GAP analysis is to check which requirements have already been implemented and where improvements are needed. Important: both the documentation and the actual implementation must be checked and a detailed action plan must then be drawn up.
Due to the involvement of a wide variety of stakeholders in cloud services, responsibilities must be defined. This includes both internal departments and other service providers, who must establish clear regulations for the implementation of the C5 requirements via service agreements. The subsequent implementation refers to the establishment of technical measures, the development of organisational processes and the creation of the necessary documentation. This step requires time, coordination and a concrete action plan before testing can begin.
Are you a cloud provider? Then follow the phases outlined above to obtain a successful BSI C5 certificate!
Are you a cloud user? Then follow the phases outlined above to systematically review your cloud provider and identify and implement any outstanding requirements!
C5 in 2025 – what has changed?
In addition to Section 393 of the German Social Security Code (SGB V), which has required BSI C5 certification for the processing of health and social data in a cloud solution since July 2025, the BSI has published a new version of the C5 in the form of a ‘community draft’: ‘Cloud Computing Criteria Catalogue C5:2025’.
With the updated version, the BSI is further developing the previous C5. In the current Community Draft, the criteria catalogue has been slightly restructured, thematically expanded and technical requirements updated to adapt to the continuing increase in cloud usage and technical changes:

As part of the restructuring process, the basic criteria are no longer accompanied exclusively by additional criteria; instead, a new logic is emerging, whereby the basic criteria are supplemented and specified by the following:
- ‘Additional Sharpening Criteria’, which specify existing requirements, for example through clearer technical or organisational specifications,
- ‘Additional Complementing Criteria’, if these were not previously covered or were insufficiently covered in the basic criteria,
- ‘Complementary Customer Criteria’, which emphasise the responsibilities and obligations of cloud customers to cooperate in accordance with the shared responsibility model.
For C5:
2025, which is structured around 17 topics, it may therefore be necessary in practice to adapt the attestations. The basic structure of attestation types 1 and 2 remains unchanged. However, it is apparent that the focus is increasingly shifting to type 2, with type 1 being regarded as a kind of transitional attestation in the development phase.
As with C5:
2020, the selection of which criteria are to be audited as part of an attestation remains the prerogative of the cloud provider. According to the BSI, the basic criteria represent the minimum standard for information security.
For companies that will need to demonstrate C5 certification in the future, C5:2025 will apply from January 2027. However, it is advisable to familiarise yourself with the new requirements and structure in advance and implement them in your organisation.
Working with adesso to achieve secure cloud operation in accordance with BSI C5
Modelling and implementing the BSI C5 criteria and bringing them into line with current technologies and best practices can be a challenge. This is exactly where adesso provides you with comprehensive support – regardless of whether you are a cloud provider on the way to certification or a cloud user.
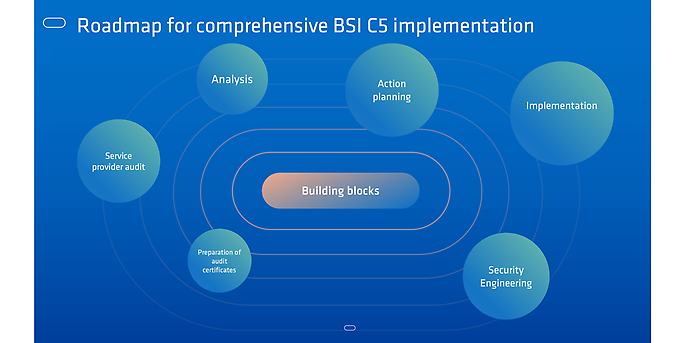
The above building blocks reflect the phases of a complete C5 implementation roadmap. They cover both technical and organisational/regulatory requirements.
adesso accompanies you throughout the entire implementation process – from the initial analysis to secure cloud operation in accordance with BSI C5. We provide comprehensive support in all relevant areas:
- Technical implementation / cloud security engineering (including): Security management
- Identity and access management
- Application and data security
- Network security
- Threat protection
- Regulatory and organisational implementation (including): Service provider audit
- Analysis of existing structures
- Action planning
- Implementation of information security requirements
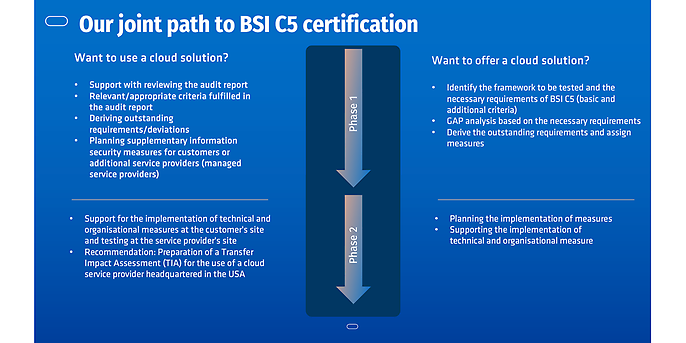
We support you!
adesso supports cloud providers and users. Our experts provide comprehensive advice, from analysis and GAP assessment to testing.

