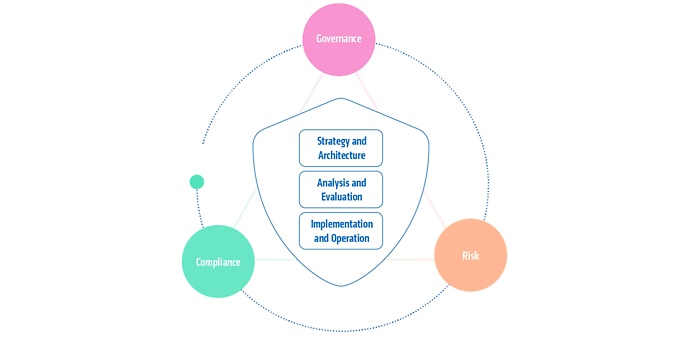
We stand for comprehensive and independent security consulting that combines strategy and practice. As a trusted advisor, we accompany our customers from analysis and design to operational implementation – always technology-independent and solution-oriented. Our expertise covers the organisational, procedural and technical dimensions of information security. This enables us to ensure that measures are implemented in accordance with regulatory requirements such as DORA, KRITIS and NIS2. Thanks to our broad network of partners, we combine in-depth expertise with practical solutions for sustainable security at the highest level.
Your advantages with adesso as your partner:
- Around 100 experienced security experts – concentrated know-how for your security
- Over 250 successfully completed projects – cross-industry experience from the field
- Trusted advisor for numerous customers – partnership-based support on an equal footing
- In-depth expertise in regulatory requirements – such as DORA, KRITIS and NIS 2
- Infrastructure and services ‘Made in Germany’ – reliable for international customers