DORA is a new EU regulation that aims to strengthen the digital operational resilience of financial entities. To meet this goal, they require robust ICT systems, well-designed processes and clear agreements with service providers. Find out more about how we can help you implement DORA and meet the requirements of this key regulation.

Digital Operational Resilience Act
DORA
DORA as the key to effective defence against cyber threats
Financial entities need to run smoothly
The DORA regulation establishes a uniform framework on how to increase IT resilience for financial entities and their IT service providers within the EU. This regulation not only helps minimise the risks of cyber attacks and technical disruptions, it also increases consumer and investor confidence in the financial sector as a whole.

Tobias Dieter, Managing Consultant in the Line of Business Information Security at adesso SE
Key topics addressed by the regulation
The ICT risk management framework enhances information risk and information security management at financial entities. The framework covers the design and operation of robust ICT systems and processes that work effectively in the event of a disruption or emergency. For that to happen, the constant monitoring of ICT risks and the establishment of safeguards must be assured. Regular testing ensures that all guidelines, plans and measures are successful in consistently maintaining stable business operations.
The testing regime for operational resilience to be conducted by companies includes planning and carrying out testing on ICT components, identifying, assessing and addressing vulnerabilities, and performing threat-led penetration tests (TLPT) on ICT services for critical functions with the direct involvement of ICT third-party service providers.
Financial entities are required to develop reliable procedures for handling ICT incidents. To meet this requirement, they have to introduce a standardised procedure for monitoring, classifying and reporting ICT incidents to the supervisory authorities.
ICT risk management includes enhanced requirements for third and fourth-party risk management. Financial entities are required to identify and appropriately address the risks posed by third-party ICT service providers. They also have to prepare and report a list of outsourced activities and include the minimum contents specified for contracts with the ICT service providers.
The regular exchange of information and intelligence on cyber threats between financial entities and regulators is vital for transparent communication.
What are the active parties?
- Credit institutions
- Payment institutions
- Account information service providers
- Electronic money institutions
- Investment firms
- Crypto-asset service providers
- Central securities depositories
- Trading venues
- Trade repositories
- Managers of alternative investment funds
- Management companies
- Data reporting service providers
- Insurance and reinsurance undertakings
- Insurance intermediaries and reinsurance intermediaries
- Institutions for occupational retirement pensions
- Rating agencies
- Crowdfunding service providers
- And so forth
There are two groups of financial entities
-
Fulfilling the strict BaFin requirements
These include banks, insurance companies, payment service providers and capital management companies.
They know the ‘regulatory IT requirements’ issued by BaFin (xAIT) that apply to them. Along with that, the firms typically have functioning management systems for information security, risks, emergencies and service providers and operate an IT service management system aligned with their needs. DORA adds a variety of other aspects to the existing topics. The challenge is to assess the new requirements and implement them correctly in the existing management systems. adesso performs a target/performance comparison with you and supports you during the evaluation and implementation of measures to manage incidents.
-
Guaranteeing a basic level of protection
It is important to run through all of the requirements.
Readiness checks have proven an excellent option here since they make it possible to meet the requirements in a structured way by asking targeted questions and making use of the answers to develop action plans. DORA defines proportionality thresholds in order to keep the effort for financial entities reasonable and differentiates between companies based on their size and revenue.
Financial entities are obliged to develop and regularly conduct mandatory ICT security and digital operational resilience training for all employees and, where appropriate, for ICT third-party service providers as well.
This training must have a level of complexity ‘commensurate to the remit of their functions’ (Art. 13(6) DORA).
ICT third-party service providers
In addition to the financial entities covered by the regulation, DORA requires their service providers to guarantee stable service provision as well. An ‘ICT third-party service provider’ is defined under Art. 3 No. 19 DORA as ‘an undertaking providing ICT services’.
ICT services’ means ‘digital and data services provided through ICT systems to one or more internal or external users on an ongoing basis, including hardware as a service and hardware services which includes the provision of technical support via software or firmware updates by the hardware provider, excluding traditional analogue telephone services.
(Art. 3 No 21 DORA)
Time procedure
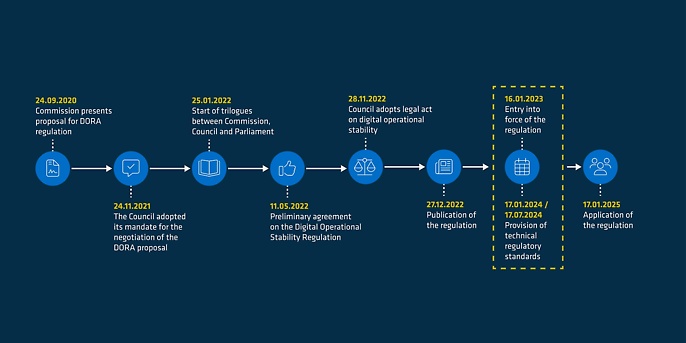
Supervisory authorities
DORA has been published but is not yet fully fleshed out.
Technical regulatory standards will be made available by the European banking supervisory authority starting in January 2024, covering the following topics among others:
- Network security
- Safeguards against intrusions and misuse of data
- Controls of access management rights
- Detection of abnormal activities and monitoring of abnormal behaviour and response processes
- ICT business continuity planning
- Review of the ICT risk management framework
- Classification of ICT-related incidents and cyber threats
- Reports of serious ICT-related incidents
- Advanced testing of ICT tools, systems and processes based on TLPT
- Key principles for sound ICT third-party risk management
- Harmonisation of the requirements for carrying out monitoring activities
Enforcement measures
EU Member States will be required to ensure that their competent national authorities effectively monitor compliance with the DORA requirements.
Fines shall be ‘effective, proportionate and dissuasive’ (Article 50(3) DORA), taking into account the circumstances of the individual case.
Public authorities may adopt any ‘type of measure, including of a pecuniary nature’ (Art. 50(4)(c) DORA) to compel financial entities to remedy breaches of the DORA requirements.
Compl.AI
Check contracts for DORA compliance quickly and easily
Automate the contract review process with Compl.AI and reduce time, costs and compliance risks. The tool analyses contracts fully automatically for DORA compliance, continuously monitors changes and ensures that your organisation is always up to date. This allows you to concentrate on your core business and ensure the security of your ICT infrastructure.
Services offered by adesso
adesso has extensive experience in the fields necessary to ensure the successful implementation of the DORA requirements. This applies in particular to information security management (ISM), information risk management (IRM), business continuity management (BCM) and provider management. Meeting all of the requirements is complex and demands the coordinated action of various business functions.
It is therefore important for financial entities and ICT service providers to take the following steps early on in the process:
Step 1 – analysis: assess requirements and determine degree of fulfilment as part of a DORA readiness check
Step 2 – action planning: identify fields of action and create a roadmap
Step 3 – implementation: implement work packages, establish them at the organisational level in project management and provide support during the implementation phase
Other topics at a glance
Do you have questions about DORA?
Contact us and let's discuss your specific challenges together.
We look forward to an exchange with you - on site or digitally.

Principal Consultant Tobias Dieter tobias.dieter@adesso.de

