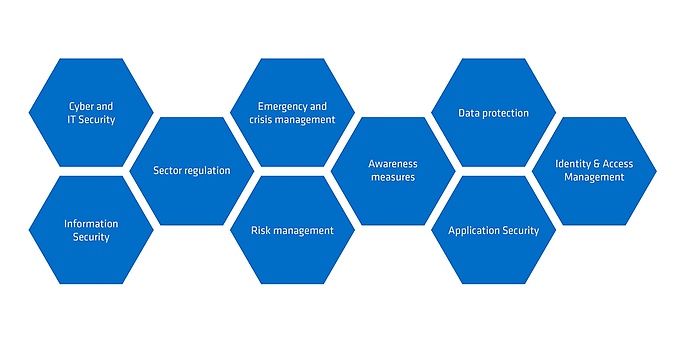
With adesso Security Services, we support the core business processes of companies by introducing targeted risk management in the context of cyber and information security. Benefit from tried and tested methods, tools and our project experience.
Challenges as drivers:
- Technological change and digitalisation: networking, mobilisation and digitalisation challenge your ability to innovate and adapt.
- Laws and regulation: non-compliance can lead to drastic penalties.
- The cloud and cybercrime: a successful cyber-attack can have consequences that threaten the very existence of companies.
- Changes in requirements and competitive situation: steadily increasing requirements to maintain the competitive position.
- Lack of skills and resources: information security means investing both in technology and in skills.
- Changing values and image: poor data protection and information security damage the corporate image.